If you’ve been around the cryptocurrency community for long, then you’ve definitely heard people preach sayings such as, “Always remember to control your private keys.” Maybe it was through a commonly said aphorism:
Your keys, your crypto; Not your keys, not your crypto.
But what does it actually mean? If you don’t understand public-private key cryptography, then those sayings offer no explanation or insight to one of the most important features of this technology: controlling the access to your value. This topic has come up a few times within the Slack community of The Bitcoin Podcast Network, so I decided it was worth explaining some basic concepts required to truly understand what this means and why it’s so important.
tl;dr: There isn’t one — you should know this if you plan to buy or use cryptocurrencies.
Cryptography 101 (and some basics of how we use them in the blockchain industry)
I strongly believe that good decision-making comes from understanding. To that end, I am going to explain some basics of what “private-keys” are, where they come from, and how we can store them. If you’re comfortable with this material already, read this and let me know if I can do a better job of explaining it to others. This is just how stuff works. I will use the way Bitcoin does things, as our example, as it has garnered the most attention and public exposure; the general process can be extended to everything else in the blockchain/cryptocurrency industry.
Public-Key Cryptography
It all starts here. Public-Key cryptography (also known as Public-Private Key or Asymmetric cryptography) is a foundational building block of blockchain technology. In order to use it, you need a pair of generated keys: one public, one private. The public-key can be passed out to others, while the private-key should be kept secret (the names should have given that part away). In general, this enables two functionalities:
- authentication — You can digitally sign data with your private-key, which can be verified by anyone who has access to the public-key. Bitcoin uses this function.
- encryption — Obfuscate data with a public-key so that no one knows what it is, which can only be converted back to its original form with the private-key. Bitcoin doesn’t use this function.
These keys can be generated by a lot of different algorithms. Bitcoin uses a specific one that uses elliptic curve mathematics, which is beyond the scope of this blog. Remember that the private-key is just a number, picked at random, between 1 and 2²⁵⁶. The public-key is then generated via some relatively complicated but well understood math. The important thing to know about this process is that it is relatively easy to do, but INCREDIBLY HARD AND NOT CURRENTLY FEASIBLE to do the opposite —i.e. you cannot create a private-key from a given public-key.
Addresses
Ok cool, you have a public-private key-pair. The next step (which is all done by wallet software for you now-a-days) is to generate an address associated with this key-pair. This is done by a specific algorithm that ensures that for every key-pair, there is a matching address. It is also important to note that you can go from the public-key to the address, but not the other way around. Just like you can go from a private-key to a public-key, but not the other way.
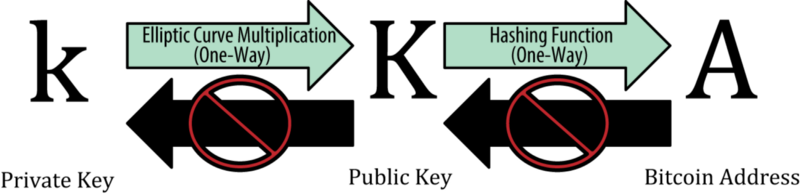
How it fits together
Your address is your identity on the Bitcoin blockchain, your private-key is how you prove your ownership of it, and your public-key is how others validate that proof.
You move Bitcoin around by creating transactions and submitting them to the network to be validated by miners. A transaction is basically a message telling the network that you want to send Bitcoin that you have associated with your address to a different address. How can people verify that you sent the transaction, you ask? The beauty of public-key cryptography allows you to authenticate the transaction by digitally signing it with your private-key.
So if I receive a signed transaction, I can use the public-key to verify that the person that signed it has control over the addresses that are sending Bitcoin without anything other than math. Here’s the key point I’m getting to:
If someone has a private-key associated with a Bitcoin address, they can move all of the funds controlled by that address with impunity, and no one can stop them.
This has a few consequences that get at the heart of why people care about this technology so much:
- You never actually hold “Bitcoins;” you hold the keys that “sign-off” on moving them around the public ledger (blockchain).
- Whoever has access to the private-keys of an associated address has access to the Bitcoin at that address. No one else.
Let’s complicate things a bit
So you can generate a key-pair at will with ease, and it is encouraged in the Bitcoin community to generate a new key-pair and address for every transaction. This drastically lowers the barrier of entry to participating in this ecosystem, as well as increases personal transactional privacy, but over time it becomes difficult to keep track of the many key-pairs and their addresses. Two quality-of-life improvements were then introduced to help this: Hierarchical Deterministic Wallets and Mnemonic Code Generation. This is how modern cryptocurrency wallets generate, manage, and backup the keys they hold.
Mnemonic Code Generation
In a nutshell, this improvement gives you a human readable (and thus memorable) way of creating a random number. Instead of trying to write down/store/remember a really long number (or its hex-representation), you can, instead, use a series of words in a particular order. The ordering of words is then uniquely mapped to a random number through an algorithm to create a private-key.
If you’ve used one of the many popular cryptocurrency wallets, they tell you to back this up and save it in a safe location. We’ll talk about this more later.
Hierarchical Deterministic Wallets
Using some tricks with cryptography and elliptic curve mathematics, a method to generate a tree of key-pairs from a single key-pair was introduced to help with the management/storage/backup of all the addresses a user has.
This enables users to focus on the security and storage of a single key-pair while simultaneously having the flexibility to use as many key-pairs as needed. This also allows for easy recovery or portability, as you only have to enter a single private-key into a new wallet to restore all of your accounts.
Putting it together
When we combine these two things, you end up with an easily memorable word combination (called a seed phrase, recovery phrase, backup code, etc) that can be used to generate any number of key-pairs. It should be stressed that this seed phrase now is the most important thing to keep safe, as whoever knows it has the ability to access and send funds from any of the private-keys that it generates.
That’s the basis of how modern wallet software generates, stores, and manages private-keys. There are more subtle details involved, but the security implications of it all is just about the same. Most notably, the seed phrase gives access to everything, and the key-pairs it generates gives access to the associated addresses. How these things are stored and who has access to them needs to be considered.
Some Important Tidbits
Custodianship
Some companies that offer services in the cryptocurrency or blockchain industry require users to send funds to them, or to an address associated with the user’s account on their platform. They then manage the private-keys on behalf of the user. Because they physically control the access to the private-keys associated with an address, they are the custodians of the funds controlled by those accounts. A user is trusting the company to not steal the user’s funds as well as manage the security of keeping those keys safe and secure from attackers.
Phishing
An important consequence of decentralization technology is that it gives the end-user more power and control over personal data. With that comes the risk and responsibility of keeping it safe from those who should not have access. Because of this, the main method of attack in the space is to try and steal credentials through phishing.
In a nutshell, phishing is an attempt to artificially recreate your login or authentication screen in order to steal your username/password to gain access your account. If you are going to use a WebApp or service to store or send crypto, you are opening yourself up to potentially being phished. Once again, if someone gains access to wherever your private-keys are stored, they can steal everything with no way of getting it back.
For more information on phishing and how to protect yourself from it, here is a blog post from the MyCrypto team:
How to Avoid Getting Scammed and Phished · Security & Phishing | MyCrypto Help & Support
Security & Phishingsupport.mycrypto.com
Questions to help guide better decision-making

Ok, now you know a few things about how keys are made and used. You should now be able to comprehend conversations about management of private-keys. This also arms you with some knowledge to make more informed decisions, most importantly, how you manage the private-keys associated with the cryptocurrencies that you hold. There is a lot more to learn, but this should give you a wide base of understanding.
There is a wide array of options available to you, and what works for your situation depends on a lot of factors. There is no single solution for everyone and everything
This decision-making process usually boils down to trade-offs among security, accessibility, and trust. A realistic scenario is having various places and methods for storing crypto which are each optimized based on the type of fund. Think about it: should you treat your walking around money the same as your life savings?
Keeping funds on an exchange
If you’re regularly trading then you’ll need access to your funds quickly. Even though cryptocurrencies have drastically decreased the time required to deposit/withdrawal funds, it still could take up to a few hours when everything is working as intended. That could mean you miss the opportunity you were looking for depending on your trading style. That said, decentralized exchanges and safer methods of using exchanges without using their custodial services is getting better over time. A good way to evaluate this is to ask yourself whether you need to move what is stored in an exchange within the response time of an hour or so. If not, then it is probably best to take it off the exchange and put it into something more secure. Here are some more questions you should ask yourself:
- Do you trade often?
- Is it a substantial amount of money for you?
- Does your account have 2FA (two-factor authentication)? Is it enabled?
- Does the exchange have a good track record of customer support? What happens if there is a problem and you need to contact them?
- Are you ok with trusting someone else with the private-keys associated with this crypto?
- What benefits could there be associated with leaving funds there?
- How much would your life be affected if the exchange disappeared overnight? What confidence do you have that this won’t happen?
Keeping funds on your personal devices
This is a vast middle-ground when it comes to storing private-keys. It can range from an encrypted vault on an air-gapped machine to having the same seed-phrase initiating wallets on all of your devices for “synced wallet” functionality. The benefit here is that you are in full control over your private-keys. The shortcomings are usually associated with shitty security practices (from either/both the user and the wallet software), and how difficult it is to properly secure a personal device from outside attackers, especially if that device is always on the internet. Here are some questions to ask yourself:
- Are your personal security practices up to snuff?
- Have you audited the devices that are storing the private-keys?
- Who else would have access to this personal device?
- Are you savvy enough to handle the potentially obscure wallet software?
- How would your life be affected if your personal device was lost or stolen?
- Do you know how the wallet software stores the private-keys it manages for you? Are they at least encrypted?
Keeping funds on a hardware wallet
Hardware wallets are currently the best way to store and maintain your private-keys, as they are reasonably accessible while never exposing the digital keys to the cess-pooly internet. That said, in order to access the funds, you will need to physically have this device — perhaps annoying for small purchases and potentially dangerous if you’re storing very large amounts (the rubber-hose approach). I usually keep the funds that I do not need to access much on hard wallets, and then make sure I securely store those hardware wallets and their associated seed phrases. Here are some questions to ask yourself:
- How often do you need to access these funds?
- Have you safely stored your seed phrase?
- Are you using the same seed phrase somewhere else? (If so, you’ve negated any security guarantees the hardware wallet has and downgraded it to the lowest security storage method.)
- Did you buy it from a reputable source? Only go through official retailers for the device you’re buying. Never buy a pre-initiated device; if you receive one, remove the funds from it and re-initiate it with a fresh seed-phrase.
Shameless self-promotion
So you’ve made it this far — well done. I hope that you’ve learned some valuable information to help you make better decisions on how you’ll interact with this amazing new technology. It isn’t easy, but it’s continually getting easier. When storing crypto, continuously think about where and how the private-keys are stored, who could gain access to them, and how you’d mitigate that. Balance that with how easily you’d like to access those funds.
As always, you can catch me, my co-hosts, and a wonderful community of individuals who support The Bitcoin Podcast Network in our Slack group. Come in and ask questions for more info, tell me about what you think I got wrong, or just generally chat with us about the tech or anything else you’re interested in. We release a lot of content throughout the network over quite a few different shows; you’re bound to find something you like!
I also work for Status.im as a security lead. Keep an eye on our mobile software (and desktop coming soon!) for secure and private messaging, an Ethereum wallet, and DApp browsing. We’re releasing a very affordable hardware wallet solution as well called the Keycard. We work based off our principles, care deeply about making this technology safe and approachable, and make technological choices that facilitate making that a reality for you. Download the beta now and join the conversation!
If you’re so inclined, donate to me to provide motivation to write more stuff like this. I have a tremendous amount of half finished blogs and ideas about writing. Your donation could push me to do more!
Stay safe out there, and stay educated!

ETH and ERC20 tokens: 0x8F53781799515e5dc8f5D00C528940cAe99aC969

BTC: 1DXmuHMufPAUEuRUwKMNLqiMqmWQyKmZP6